As part of an ongoing effort to ensure all systems are secure, we are now adding a zero-trust approach to your security stack. As attackers become more sophisticated, so do the complexities in stopping software-based threats.
Large governments and other enterprise organizations regularly adopt the techniques and solutions we are implementing. As your managed service provider, we understand that using a higher grade of security is fundamental in protecting you from the latest threats.
What is Zero Trust?
Zero Trust is a security framework that states that organizations should not trust any entity inside or outside their perimeter at any time. Today’s environment must provide the visibility, and IT controls needed to secure, manage and monitor every device, user, app, and network used to access business data.
ThreatLocker® Helps With:
• Layered Security
• Ransomware Prevention • Compliance
• Internal Disputes
• Storage Control
• Data Privacy
Today, ThreatLocker® will be running on your PCs, blocking any unapproved software, including ransomware, viruses, and other malicious software.
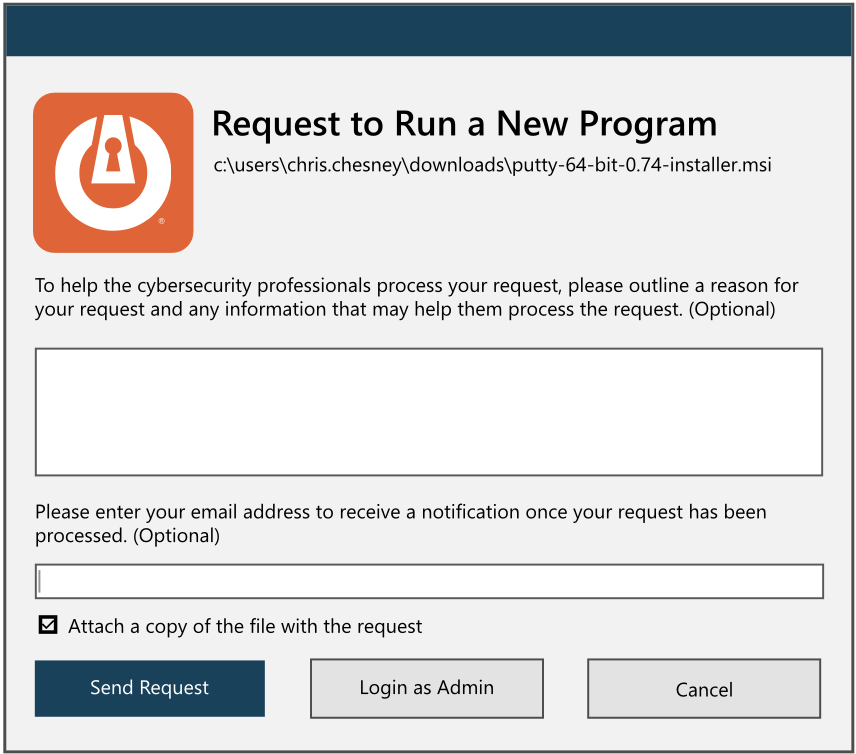
Should you run applications that are not approved, you will receive a notification prompting you to request permission or ignore it if it’s not needed for your day-to-day business functions.
Selecting the “Request Permission” button will notify us. We will review the request, ensure the application is not malicious and approve it if appropriate.
As such, it is vital to inform us in advance if you need any new software installed by entering a ticket with the service desk.